Please wait.
Article
Securifyer: innovative methods to achieve Optimal Return On Security Investment (ROSI)
Radar Risk is proud to announce the launch of Securifyer™: innovative methods built to support organizations in managing potential security risks. The ultimate goal is to safeguard people's safety and to protect the achievement of objectives.
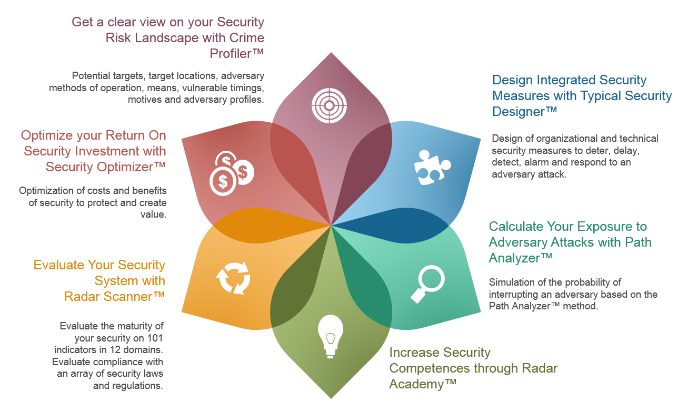
Crime Profiler™
If security risk scenarios that may affect your objectives are not clearly identified, analyzed and evaluated, the risk exists that some security risk scenarios are not, under- or over-secured.
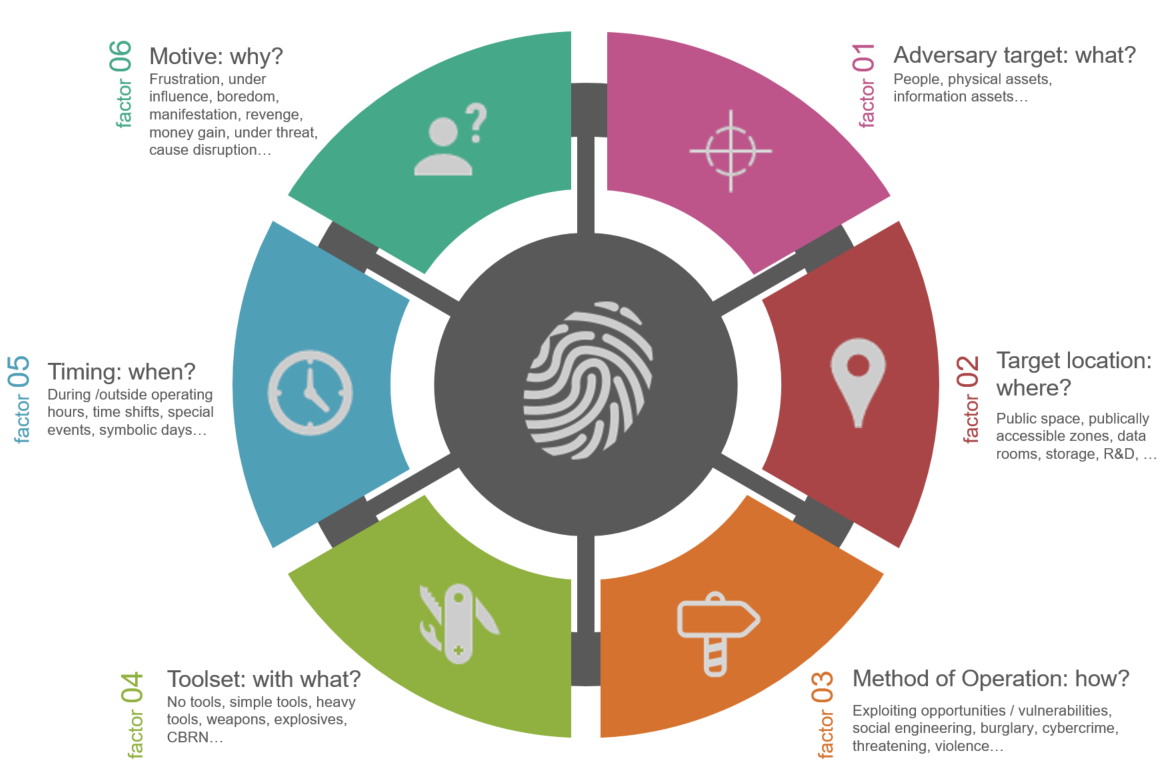
With the Crime Profiler™ method, organizations get a clear view on their Security Risk Landscape. The method profiles an Adversary by identifying potential targets, target locations, methods of operation, toolset, timing and motive. Together, these elements form a security risk 'scenario'.
Typical Security Designer™
If security measures in place do not effectively deter, detect, alarm, delay or respond to security incidents, the risk exists that scarce resources are allocated on the wrong security measures.
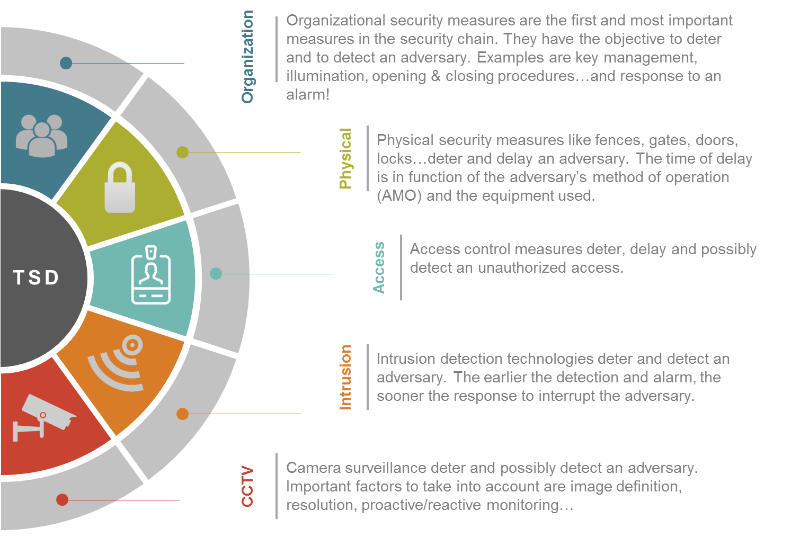
Typical Security Designer™ is a method that designs and/or reviews security measures based on organizational measures, physical security, access control, intrusion detection, camera surveillance, alarm handling and response.
Path Analyzer™
If security measures in place do not effectively deter, detect, alarm, delay or respond to security risk scenarios, the risks exists that the probability of interrupting an adversary may not meet the risk tolerance level.
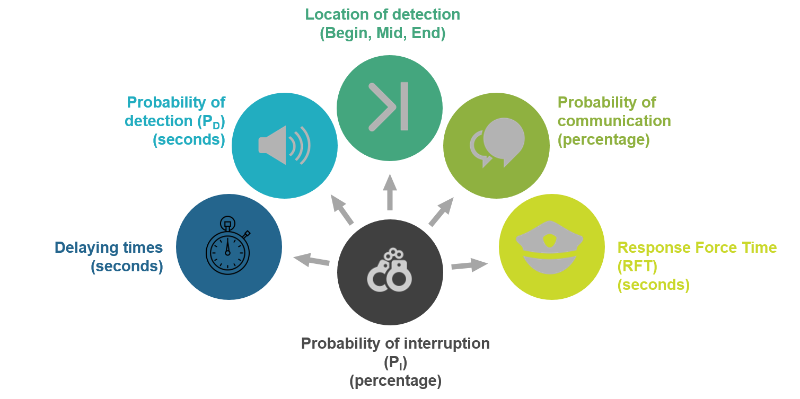
Path Analyzer™ is a method that calculates the Probability of Interrupting an adversary based on: delaying times, probability of detection, location of detection, probability of Alarming and Response Force Times.
Radar Academy
Competences in assessing security risks, designing integrated security measures, evaluating exposure to Adversary attacks can be aquired or increased through a variety of courses organized by the Radar Academy.
Security Radar Scanner™
If there is no mature security management system in place, the risk exists that security risks that may affect your objectives are not properly managed.
Security Radar Scanner™ is a method that evaluates the maturity on 101 indicators in 6 security domains.The compliance of the security management system can be evaluated against numerous security regulations such as ISPS, C-TPAT, AEO...
Security Optimizer™
If an organization has a clear view on the Security Risk Landscape and capital and operational expenditures in security, then these insights can be evaluated by Security Optimizer™. This method calculates the 'security optimum': the optimal Return On Security Investment (ROSI).
All Securifyer™ methods are available as Security Risk Management software, empowered by Enablon.
For more information, you can contact us here.
